This website stores cookies on your computer. These cookies are used to collect information about how you interact with our website and allow us to remember you. We use this information in order to improve and customize your browsing experience and for analytics and metrics about our visitors both on this website and other media. To find out more about the cookies we use,
see our Privacy Policy.
Open House • Learn how you can grow your career with us! • May 15 • 3:00–6:00 p.m. • Merrimack, NH
Jamf Showcase
Manage and Secure Apple at Work
Jamf Is Trusted by IBM, SAP, Ohio State, and over 71,000 Other Businesses, Hospitals, and Schools
Every day, Jamf is responsible for helping organizations maximize their tech initiatives by protecting and managing over 30 million Apple and Android devices worldwide.
MANAGE Devices
- Zero touch deployment
- Mobile device management (MDM)
- Application management
- Inventory management
- Self-service through a company-owned app catalog
SECURE Endpoints and Network Access
- Identity and access management
- Endpoint protection
- Threat prevention and remediation
- Content filtering and safe Internet
- Zero trust network access (ZTNA)
- Security visibility and compliance
Jamf’s portfolio of Apple‑focused solutions:
Jamf’s portfolio of Apple‑focused solutions:
Jamf Pro
Whether you have used Apple for years and have 10,000 users in your organization, or you are just beginning to integrate Apple devices into your organization—Jamf and Jamf Pro make management simple, secure, and cost effective. IT admins gain peace of mind and users get the experience they want.Today, more organizations than ever before are examining their remote employee and work-from-home policies—be it for health, employee retention or employee productivity reasons. Jamf can help make it a reality. In this eBook, Jamf explains how you can best serve employees and organizations.
Jamf Connect
More employees than ever are working from different locations and on various devices. Jamf Connect safely bridges workers to the devices, apps, and data they need to be productive in the modern world, while empowering IT with the ability to remotely manage users, groups, passwords, and access to corporate applications and cloud resources.With Jamf, you can ensure the right users are on compliant devices and are accessing authorized resources—no matter where they are. This evolved approach to identity and security management eases the burden on IT staff and end users. Jamf Connect allows for simple provisioning of users from a cloud identity service during an Apple provisioning workflow, complete with multi-factor authentication and access controls.
Account Provisioning
Whether it’s during setup or in day-to-day use, Jamf Connect ensures a single cloud identity through Okta or Microsoft Azure is being used to access an employee’s device and applications—without the need to bind it to Active Directory.Application-based Microtunnels
Enforce least privilege access and prevent lateral network movement (a common vector for security breaches) by only connecting users to the apps they are authorized to access.Password Synchronization
Jamf Connect ensures a user’s cloud identity passwords are synchronized down to the local account level—even when the password is changed.Risk-aware Access Policies
Enhance security by preventing access from users and devices that may be compromised.Identity Management
Enable user authentication through single sign-on (SSO) so you don’t have to manage certificates. Keep an eye on all company devices, who is accessing them, when, and from what device. This is all done without impacting battery life—and operates silently in the background without interfering with the user experience. Get peace of mind knowing both the device and corporate information are protected.Unified Access Policy
Jamf Connect makes deploying servers, managing certificates, and configuring IP addresses a thing of the past. It spans all hosting locations (on-premises, private and public clouds, and SaaS applications), all modern operating systems, and all management paradigms. After a user authenticates on their device, business connections are secured while enabling non-business applications to route directly to the Internet, preserving end-user privacy and optimizing network infrastructure.Jamf Protect
Jamf Is Trusted by IBM, SAP, Ohio State, and over 71,000 Other Businesses, Hospitals, and Schools
Protect users, devices, and organizational data from malicious intent while automating, enforcing, and managing data usage and consumption policies. Jamf Protect provides a complete solution for maintaining compliance, addressing antivirus needs by preventing macOS malware, and detecting / remediating Mac-specific threats. It also protects iOS endpoints from being compromised through mobile threat detection and zero-day phishing prevention with a first-class app for notifications and remediation. Security like this is created with Jamf’s Apple-first approach, but protects other mobile devices—such as Windows or Android—just as well.Jamf Protect helps enforce consistent policies for better and more cost-effective management. Corporate mobile devices provide the freedom to work anytime, anywhere—but the rise of streaming services are causing data pools to drain rapidly. Jamf empowers organizations to enforce acceptable usage policies to eliminate shadow IT and block risky content—all while managing data consumption with real-time analytics and granular reporting.
Endpoint Protection
Purpose-built for Apple, Jamf Protect secures devices from threats to keep data safe.
Purpose-built for Apple, Jamf Protect secures devices from threats to keep data safe.
- Anti-malware prevents known and new variants of malware from running on Mac devices
- On-device protection blocks new and zero-day threats through behavioral analysis aligned with the MITRE ATT&CK framework for macOS and on-device security detection for mobile devices with the Jamf Trust app
- Removable storage controls ensure that only approved or compliant external storage devices can be connected
- Application restrictions define applications or developer IDs that should be blocked, hidden, or otherwise prevented from running on a device
Threat Prevention and Remediation
Protect users from threats like phishing attacks and other cyber threats that put organizational and personal data at risk.
Protect users from threats like phishing attacks and other cyber threats that put organizational and personal data at risk.
- Web-based prevention for phishing and ransomware keeps threats from impacting protected users and devices
- MI:RIAM—Jamf’s advanced machine learning and threat intelligence engine—evaluates unknown domains in real time to block likely threats
- Remediation with Jamf Pro integration offers a variety of options for streamlining or automating required actions after a threat is detected
- Integrates with your security incident and event management solution (SIEM) or security orchestration, automation, and response (SOAR) solutions
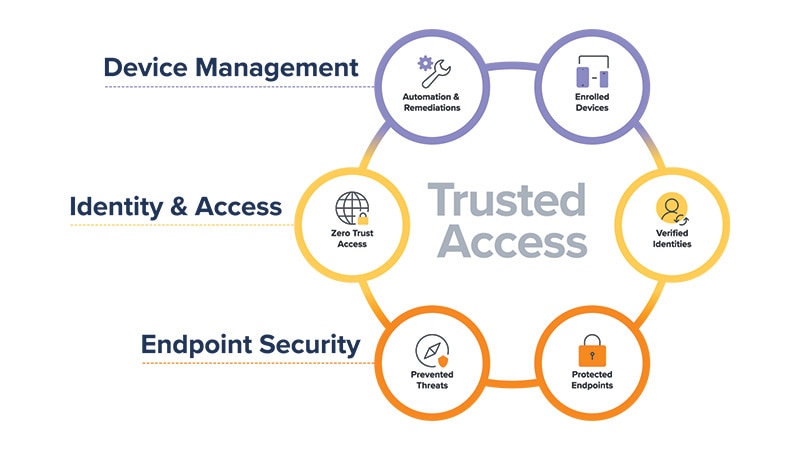
Jamf Trusted Access
Risks come in many shapes and forms. By ensuring that only enrolled, verified devices can gain access to work resources, organizations can dramatically enhance the security of their data to create an experience users love and a workplace organizations trust.Organizations can achieve trusted access by:
- Requiring only authorized users are granted access on enrolled devices
- Providing a secure connection to corporate apps and data
- Delivering comprehensive modern security to defend against an evolving threat landscape
Jamf School
Educators strive to provide the best learning experience for students and prepare them for the world. Jamf School is a purpose-built mobile device management solution (MDM) that gives you the ability to deploy and manage Apple devices—the best learning technology—with ease, so you can focus on your mission of teaching students. Its intuitive Web-based interface makes deploying, managing, and securing Mac, iPad, iPhone, and Apple TV simple. Easily create and manage users, user groups, and device groups. View in-depth information and perform diagnostics on individual devices.Dashboard
Keep track of managed devices, users, and apps. Access devices quickly and easily and identify issues for remediation.Classroom Management
Classes can be easily managed by dragging and dropping the required apps and content and creating restrictions. With App Request, teachers can request apps from Jamf School, which are then shared with IT admins.iBeacon Profile Assignment
Enable automatic assignment of profiles using iBeacon technology. Students gain automatic access to subject-specific materials, while unrelated content is hidden.Incident System
Use the Incident System to keep track of whether and when devices have been damaged or other possible problems have been detected.Locations
Tackle multiple locations or schools easily. With location support, manage each location and its devices, users, and groups separately—pushing profiles, apps, updates, and more—from a single location.Content Caching
Avoid slow Internet connections when everyone in the same class needs to download the same file at the same time. Download files that will be used by multiple students to one dedicated device that goes on to serve others.Additional Resources
Apple Device Management for Beginners
Download this eBook for a overview of all the many integrations between Jamf and Microsoft. Jamf is a member of the MISA (Microsoft Intelligent Security Association) and this document includes links to documentation, customer quotes, descriptions of the integrations, and how Trusted Access can be achieved.
Identity Management for Beginners
Identity Management is an aspect of IT that is becoming commonplace. But, as the technology world advances, and the needs of employees move with them, it's important that organizations establish their workflows in ways that are both modern and future-proof. Download this eBook and discover how Jamf MDM and Jamf Connect help organizations take a significant step toward modern identity management.
Mac Endpoint Protection for Beginners
For decades, Mac has been known as the most secure out-of-the-box device on the market. Apple’s native security functionality continues to provide the greatest starting point for the enterprise, but it’s only the beginning. Download this eBook to learn what Mac-focused endpoint protection means, its capabilities, and how to best protect your fleet.
Jamf and Microsoft: Managing and Securing Apple in the Enterprise
Download this eBook for an overview of all the many integrations between Jamf and Microsoft. Jamf is a member of the MISA (Microsoft Intelligent Security Association) and this document includes links to documentation, customer quotes, descriptions of the integrations, and how Trusted Access can be achieved.
Let’s Connect!
You’ve got questions. Let’s find the answers together. Fill out the form below and we’ll get you the information you need.Read Transcript
Batch Add Products by Item #
11